Learn from our experts
Designing secure IoT products
Creating secure products with ease
The industry is coming together to create streamlined best practices, frameworks, and certifications. Nordic aligns with PSA CertifiedTM to provide a standardized approach to security that guides customers through their individual security journey. Below we have highlighted a few simplified steps, guiding you towards a successful result:
Analyze - Threat models & security analysis
Architect - Hardware & firmware specifications
Implement - Firmware Source code
Certify - Independently tested
Security goals and objectives
At Nordic we have a clear goal when it comes to security. Enable everyone to design and deploy secure products, by:
- Making the right choices from the start.
- Understanding the threats and value of security
- Protecting critical assets against common threats
IoT product security can be divided into a few simple objectives every product should meet.
Secure boot and secure update with anti-rollback
Isolation between secure and non-secure environments
Secure storage
Attestation and unique identification
Security Lifecycle
Cryptographic services
Learn more
Security device uses Nordic nRF5340 to determine and report unauthorized door access

Artifeel’s Check’In employs Nordic nRF5340 SoC to run Zephyr RTOS for ML prediction model and enable Bluetooth LE for future features.
Learn more
An Introduction to Trusted Firmware-M (TF-M)
Nordic Semiconductor recommends following the PSA Certified IoT Security Framework in your product development process. The four-step process of analyze, architect, implement, certify, provides a framework to guide your decisions from concept to production to ensure an appropriate level of security is implemented in your IoT device.
Learn more
Securing IoT products with PSA Certified APIs
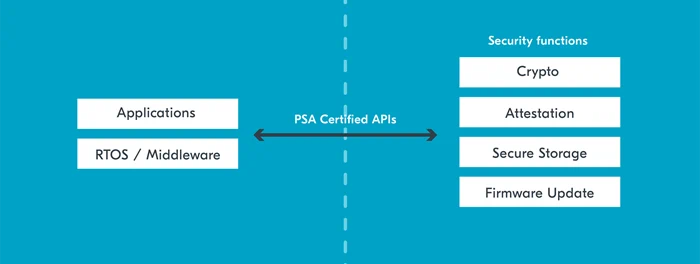
Internet-of-Things (IoT) devices are designed to connect to the internet and/or exchange information with other devices, making them a target for hackers who can exploit security vulnerabilities. Implementing robust security measures to ensure data integrity, confidentiality, and availability on those devices has become a priority.